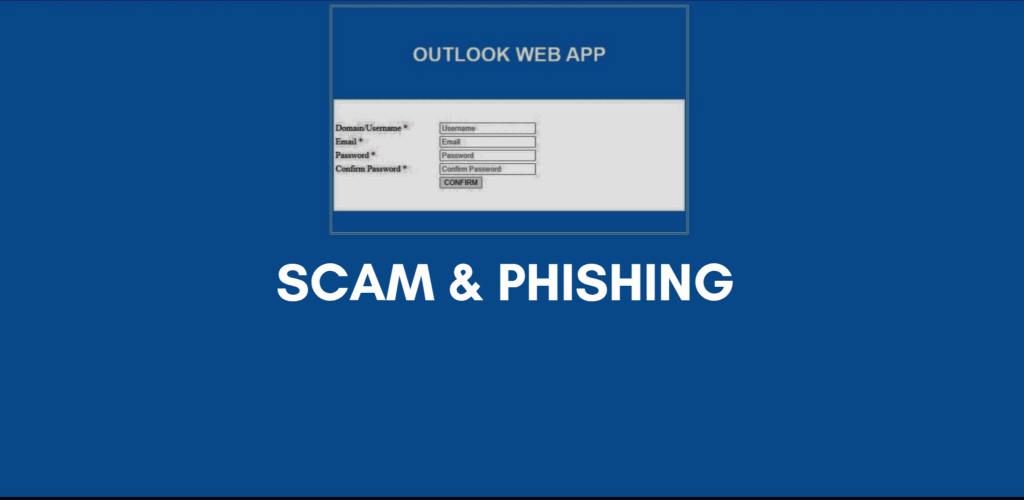
Over the past week, I’ve encountered a troubling wave of phishing emails sent to my official .hr address—the same one I use for my website—and each message claimed to originate from a reputable Croatian national service using Microsoft Outlook. In three separate instances, I found a yellow‐highlighted link in the body of the email that led to what looked like an Outlook Web login page (as shown in image here). A quick check on VirusTotal and a DNS lookup confirmed that each URL was hosted on a newly registered server known for scam activity. Despite this, the attackers have grown so complacent that the fake login pages no longer even resemble the real Outlook interface, making the entire affair almost comical.
What I observed is that these phishing campaigns have spread like wildfire, systematically targeting national companies and government agencies across Croatia. The emails themselves bear no official branding or personalization (example is linked here); they simply instruct you to log in or update your account via the provided link. Should you take the bait, your credentials are immediately harvested, granting the attackers full access to your Microsoft 365 and Outlook accounts, as well as any other connected services. From there, the compromised account is used to launch a fresh wave of phishing emails to everyone in your contact list, triggering a relentless chain reaction throughout your network.
The danger lies not in glamorous or elaborate social engineering, but in sheer volume and our innate trust in familiar institutions. These attacks have become more frequent, yet paradoxically less sophisticated. By preying on our reflexive response to “urgent” account alerts, the phishers hope to bypass careful scrutiny and clear the lowest bar for deception.
To defend yourself, treat every unexpected email link with skepticism. Before clicking, hover over the sender’s address to confirm it matches the supposed domain, and inspect the URL for discrepancies. If you suspect a phishing attempt, report it immediately to your IT department. For those comfortable working with email headers and malicious links, forward the details to CERT.hr; otherwise, simply flag the message as suspicious so that security professionals can investigate. Equally important is spreading the word: share your experience with colleagues and remind them that awareness is our strongest shield against these attacks.
A case in point was an email I received from “Meteo.hr.” After verifying the domain’s legitimacy through CARNet’s Domene.hr database, I discovered that it was indeed a genuine, uncompromised domain. Yet the message still slipped past spam filters and landed in my primary inbox—a stark reminder of how attackers exploit trusted brands to evade detection.
As these phishing campaigns continue to sweep through Croatian institutions, let’s all play our part in safeguarding our digital infrastructure. If you work for national agency, please circulate this warning and reinforce the importance of vigilance. Above all, stay safe online and remember to pause—and double-check—before you click. 🛡️
Cover image is my own screenshot from VM edited in Canva, while text was proofreaded and checked for clarity using Preplexity Pro AI.